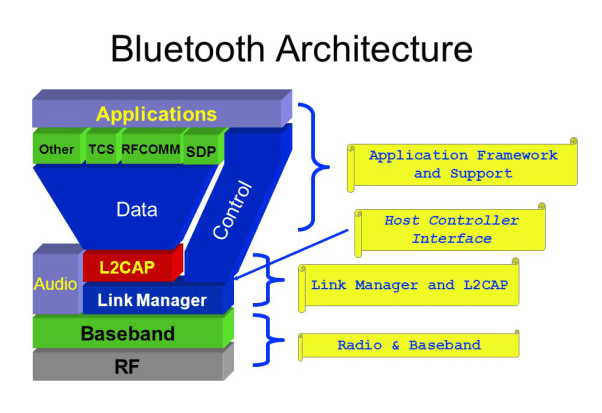
Bluetooth layers and Protocol Stack
- Bluetooth standard has many protocols that are organized into different layers.
- The layer structure of Bluetooth does not follow OSI model, TCP/IP model or any other known model.
- The different layers and Bluetooth Protocol architecture.
Radio Layer
- The Bluetooth radio layer corresponds to the physical layer of OSI model.
- It deals with ratio transmission and modulation.
- The radio layer moves data from master to slave or vice versa.
- It is a low power system that uses 2.4 GHz ISM band in a range of 10 meters.
- This band is divided into 79 channels of 1MHz each. Bluetooth uses the Frequency Hopping Spread Spectrum (FHSS) method in the physical layer to avoid interference from other devices or networks.
- Bluetooth hops 1600 times per second, i.e. each device changes its modulation frequency 1600 times per second.
- In order to change bits into a signal, it uses a version of FSK called GFSK i.e. FSK with Gaussian bandwidth filtering.
Baseband Layer
- Baseband layer is equivalent to the MAC sublayer in LANs.
- Bluetooth uses a form of TDMA called TDD-TDMA (time division duplex TDMA).
- Master and slave stations communicate with each other using time slots.
- The master in each piconet defines the time slot of 625 µsec.
- In TDD- TDMA, communication is half duplex in which receiver can send and receive data but not at the same time.
- If the piconet has only no slave; the master uses even numbered slots (0, 2, 4, …) and the slave uses odd-numbered slots (1, 3, 5, …. ). Both master and slave communicate in half duplex mode. In slot 0, master sends & secondary receives; in slot 1, secondary sends and primary receives.
- If piconet has more than one slave, the master uses even numbered slots. The slave sends in the next odd-numbered slot if the packet in the previous slot was addressed to it.
- In Baseband layer, two types of links can be created between a master and slave. These are:
- Asynchronous Connection-less (ACL)
- It is used for packet switched data that is available at irregular intervals.
- ACL delivers traffic on a best effort basis. Frames can be lost & may have to be retransmitted.
- A slave can have only one ACL link to its master.
- Thus ACL link is used where correct delivery is preferred over fast delivery.
- The ACL can achieve a maximum data rate of 721 kbps by using one, three or more slots.
- Synchronous Connection Oriented (SCO)
- sco is used for real time data such as sound. It is used where fast delivery is preferred over accurate delivery.
- In an sco link, a physical link is created between the master and slave by reserving specific slots at regular intervals.
- Damaged packet; are not retransmitted over sco links.
- A slave can have three sco links with the master and can send data at 64 Kbps.
Logical Link, Control Adaptation Protocol Layer (L2CAP)
- The logical unit link control adaptation protocol is equivalent to logical link control sublayer of LAN.
- The ACL link uses L2CAP for data exchange but sco channel does not use it.
- The various function of L2CAP is:
- Segmentation and reassembly
- L2CAP receives the packets of upto 64 KB from upper layers and divides them into frames for transmission.
- It adds extra information to define the location of frame in the original packet.
- The L2CAP reassembles the frame into packets again at the destination.
- Multiplexing
- L2CAP performs multiplexing at sender side and demultiplexing at receiver side.
- At the sender site, it accepts data from one of the upper layer protocols frames them and deliver them to the Baseband layer.
- At the receiver site, it accepts a frame from the baseband layer, extracts the data, and delivers them to the appropriate protocol1ayer.
- Quality of Service (QOS)
- L2CAP handles quality of service requirements, both when links are established and during normal operation.
- It also enables the devices to negotiate the maximum payload size during connection establishment.
Bluetooth Frame Format
The various fields of blue tooth frame format are:
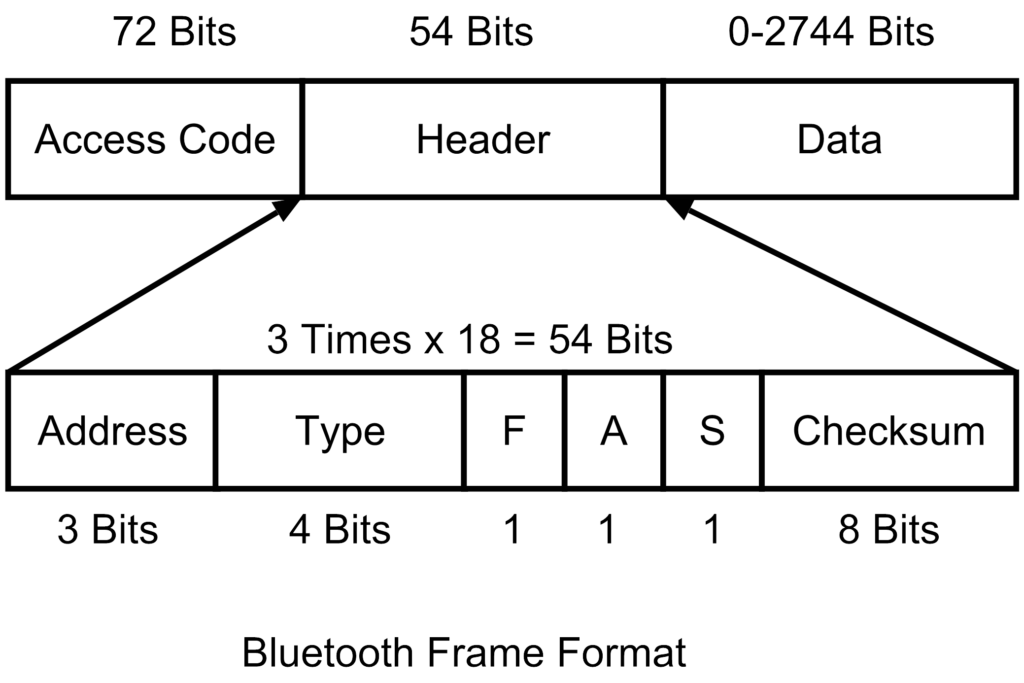
- Access Code: It is 72 bit field that contains synchronization bits. It identifies the master.
- Header: This is 54-bit field. It contain 18 bit pattern that is repeated for 3 time.The header field contains following subfields:
- Address: This 3 bit field can define upto seven slaves (1 to 7). If the address is zero, it is used for broadcast communication from primary to all secondaries.
- Type: This 4 bit field identifies the type of data coming from upper layers.
- F: This flow bit is used for flow control. When set to 1, it means the device is unable to receive more frames.
- A: This bit is used for acknowledgement.
- S: This bit contains a sequence number of the frame to detect retransmission. As stop and wait protocol is used, one bit is sufficient.
- Checksum: This 8 bit field contains checksum to detect errors in header.
- Data Field: This field can be 0 to 2744 bits long. It contains data or control information coming from upper layers
States/Mode of Bluetooth: –
- Active mode: It enables master slave communication (limited to 7 devices).
- Hold mode: It frees the slave for a predetermined one time old period.
- Sniff mode: It frees the slave for predetermined, recurring fixed time periods.
- Park mode: It enables a master to connect to as many as 255 devices in addition to 7 active devices.(It is a process of temporarily deactivating a device to allow its active member addresses to be removed or probably re-assigned)
(Visited 8,388 times, 1 visits today)
Bluetooth Architecture
I like the article
Thanks for posting this article. Its indeed a good explanation about bluetooth architecture.
Can you please brief about all other layers and profiles, audio routing etc?